An insider threat is a person with inside knowledge of or access to an organization’s resources, who then uses that privileged knowledge or access to cause harm to the organization.
When it comes to SaaS, an insider threat is when a person who has been granted access permissions to the organization’s SaaS applications or data uses that access to cause harm.
An insider threat is any individual with authorized access to an organization’s systems, data, or networks who uses that access (intentionally or unintentionally) to cause harm. In SaaS ecosystems, this threat typically comes from users granted permissions within SaaS applications who exploit that access to compromise sensitive assets.
Insider threats are uniquely dangerous because they don’t always look like threats. They often come from trusted users (employees, contractors, or service accounts) who already have access.
The Three Faces of Insider Threats
Not all insider threats are created equal. In fact, one of the biggest challenges in detecting them is that they don’t follow a single pattern. The motivations and behaviors behind insider risk can vary, but most fall into three key categories:
- Malicious insiders – These are users with intent to harm. They might steal data, sabotage systems, or leak sensitive information for financial or competitive gain. Think of a disgruntled employee that was terminated, and wants to sell proprietary code or roadmaps to a competitor.
- Negligent insiders – Often well-intentioned, these users accidentally expose data through carelessness. Think of a regular, hard-working employee at your organization. They are just trying to do their job, but don’t know the security risks behind miniscule & seemingly harmless actions they take. For example, instead of sharing an asset directly with a user, they set it to 'Public,' meaning anyone with the link can access it. We see this time and time again with extremely sensitive information such as salaries, budget files, and more.
- Compromised insiders – These company accounts have been hijacked by external actors. Think of a stereotypical evil hacker from a movie that is trying to do some serious damage. These threats often manifest via phishing, credential stuffing, or stolen OAuth tokens. Though the activity comes from a trusted account that looks legit (since it’s probably a domain from your company in most cases), the user behind it is not who you think it is.
Each of these types represents a serious risk – but it’s the blending of categories that makes detection especially tricky. A careless employee might fall victim to a phishing email, turning a negligent insider into a compromised one overnight. In SaaS environments, where access is fluid and often over-provisioned, that shift can go undetected for weeks.
Common Types of Insider Threats in SaaS Ecosystems
Who can pose as an insider threats within your organization? The most common three are:
- Employees
- Third party collaborators
- Former employees
Employees
Employees have access to the entire SaaS ecosystem. Even the most well intentioned employees can become a threat through basic misuse, lack of education, or lack of awareness. Especially in specific environments like Google Workspace, user behavior can negatively impact an organization's security.
Third-Party Collaborators
The nature of SaaS is the ease of collaboration, especially when working with third parties, vendors, or contractors. Any external party that an employee needs to collaborate with can potentially be made an insider.
These potential insiders can include:
- Contractors
- Service providers
- Suppliers
- Customers and clients
- Partners
Former Employees
Former employee access is a detrimental threat to an organization's data security. In the world of SaaS and cloud collaboration, data can live far beyond the lifecycle of an employee. Every file shared, every folder link sent, every app integrated into your stack can become a lingering risk once that person is gone.
During offboarding, most companies focus on IT processes like disabling accounts or reclaiming laptops, but what about those public links left open in Google Drive? Assets shared with personal email addresses? That one Slack guest account that never got revoked?
There’s usually always security gaps in the offboarding process. If you’re not actively managing these permissions after employees leave, you could be facing serious data leaks, regulatory violations, or competitive intelligence going straight into the hands of competitors.
What Insider Threats Look Like in SaaS Apps
SaaS applications are designed for collaboration and speed – which makes them a goldmine for identity-based abuse if not properly monitored. Insider threats in these environments don’t always wave red flags. They often appear as routine activity, unless you know what patterns to look for and how to interpret them in context.
Here are a few common identity-driven behaviors that signal insider risk:
- Mass file downloads or sharing outside the organization – A potential sign of data exfiltration, especially if done in a short time frame or by a user not typically accessing large volumes of data.
- Use of OAuth tokens to grant third-party access – While OAuth is essential for productivity tools, excessive or unusual app authorizations to third-party shadow apps can be a sign of misuse or compromise.
- Sharing files with personal or non-corporate email addresses – This may indicate accidental exposure or an intentional attempt to move sensitive data outside company control and oversight.
- Access to data outside normal role or department boundaries – This is when someone is trying to access something they have no business in doing. For example, a marketing contractor downloading financial reports, or a product engineer accessing HR documents.
- Former employees or contractors with lingering access – As previously mentioned, without automated offboarding or app-level access reviews, stale accounts often remain active and exploitable. This scenario is especially prevalent in organizations who use Google Workspace in their SaaS stack. After work with contractors is done, these files are rarely unshared, and permissions are granted permanently.
How DoControl Approaches Insider Threat Monitoring
DoControl’s Identity Threat Detection and Response (ITDR) module is purpose-built to protect SaaS environments from identity-based threats – especially those originating from within.
We integrate with your HRIS and IdP systems to collect data on all your identities, connecting the dots to who they are at the user level and what actions they’re taking in SaaS.
Our approach centers on visibility, context, and real-time, user-level control.
Identity Threat Detection & Response
We build a risk profile for every identity in your SaaS ecosystem by aggregating signals from user behavior, file access patterns, SaaS permissions, and business context like department and role data from HRIS systems.
This enables teams to move beyond surface-level alerts and prioritize actual exposure based on user intent and impact.
Within the DoControl dashboard, you gain a comprehensive view of each identity’s risk profile – including recent alerts they’ve triggered, the assets and applications they’ve accessed, where and how they accessed them, and the devices used.
You can also see all activity from the past 30 days, including connections to unsanctioned or shadow applications. No stone is left unturned, giving you more visibility into user behavior and identity risk across your SaaS environment than you thought was possible!
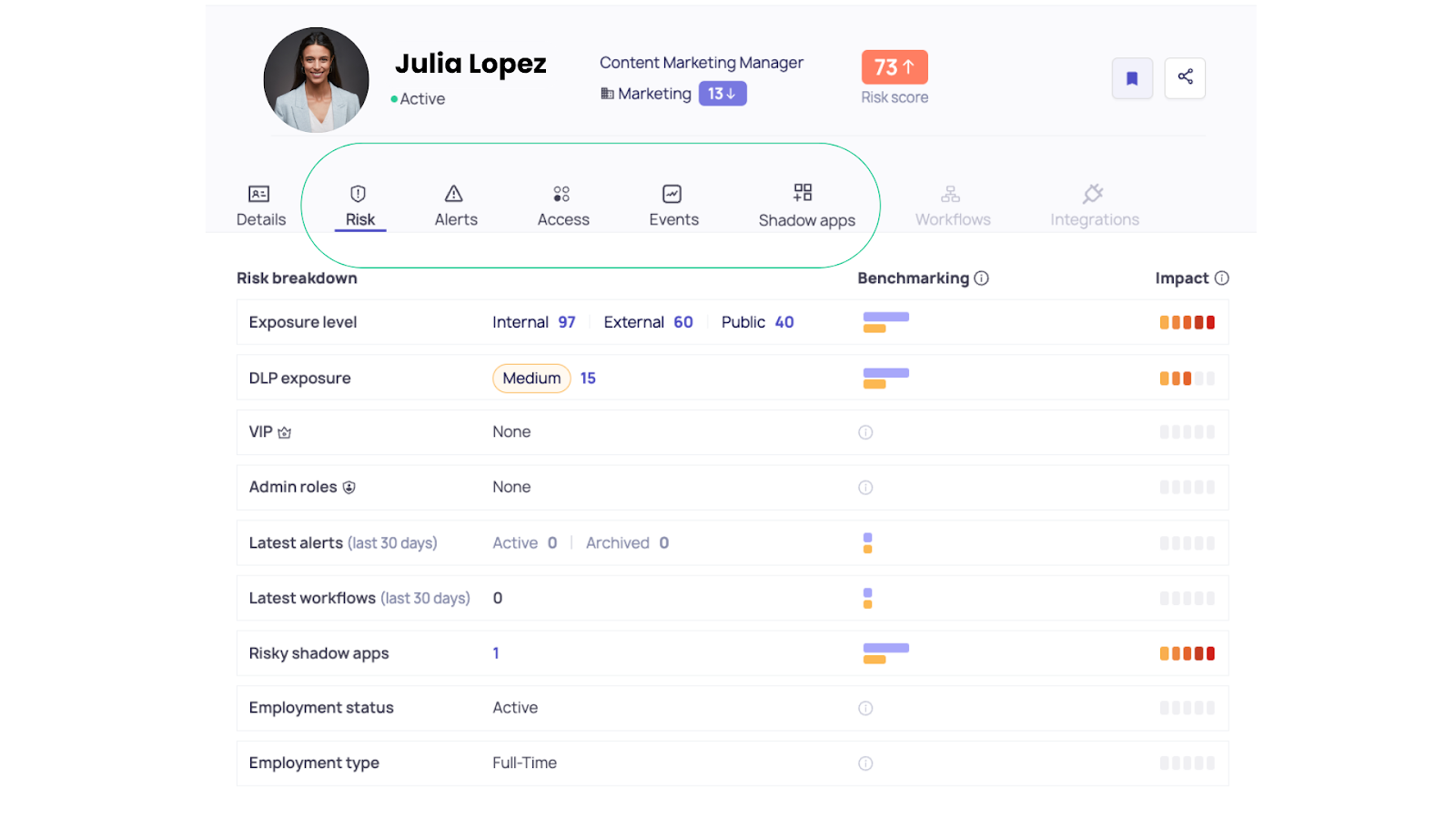
User Behavior Anomaly Detection
DoControl continuously monitors user activity and benchmarks it against department- and role-specific norms.
When behavior deviates – such as a sudden spike in file sharing, an inactive user initiating a high volume of OAuth connections, or an admin performing actions outside their typical scope – our platform detects and flags it in real time, enabling swift investigation and response.
This is especially powerful in how we capture and track unusual access and login patterns. For example, if an employee logs in from California one minute, then Europe 20 minutes later, we know that there is some sort of suspicious activity happening under their identity. From there, we immediately notify security teams, enabling them to jump on the threat and remediate the risk immediately.

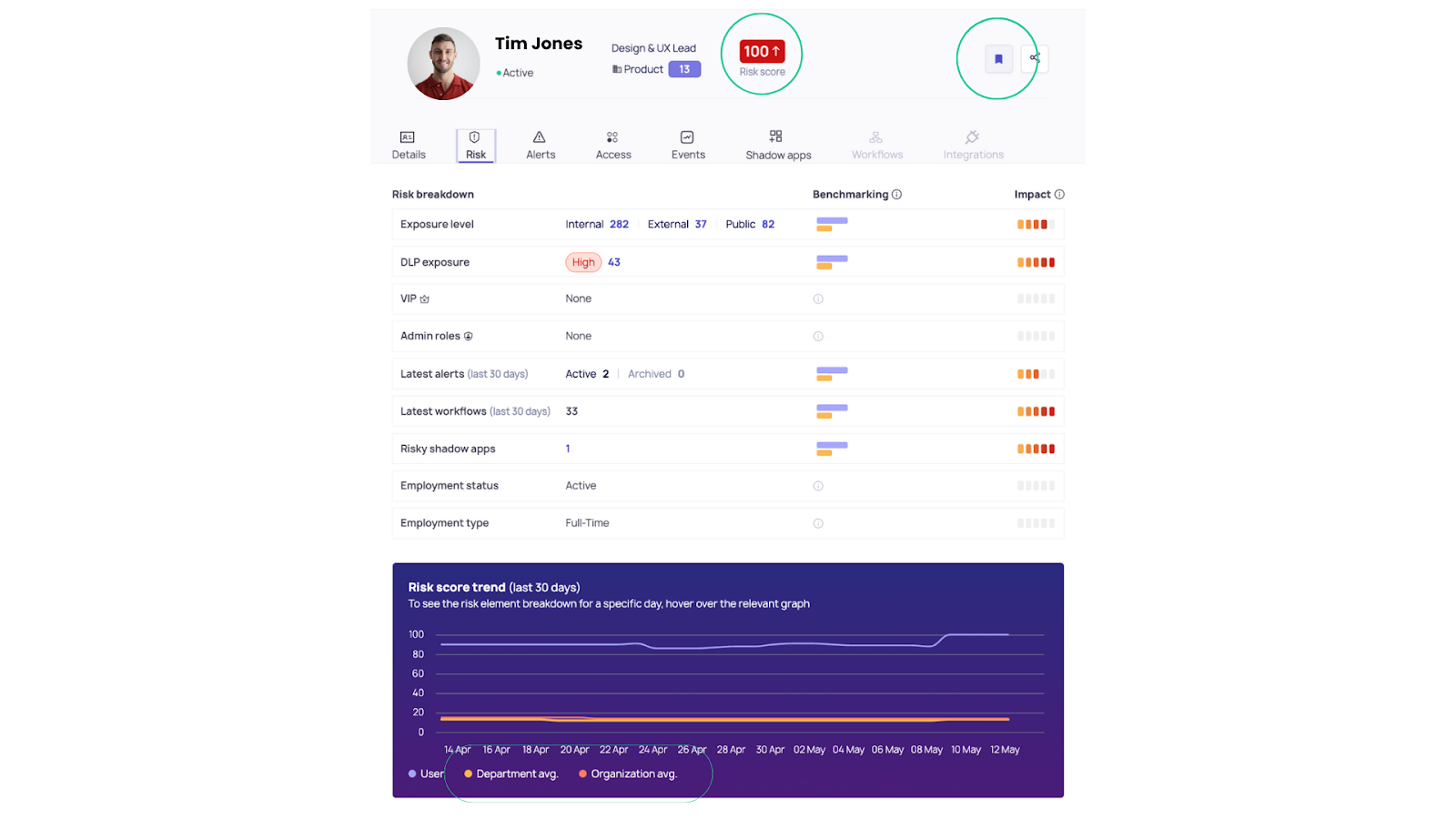
Dynamic Risk Scoring
Each identity is scored based on a blend of behavior, access level, context, and deviation from norms. The score is not static, it evolves alongside the user’s actions, adjusting as new signals are ingested.
The dynamic risk score is a key part of our product that reflects not only the likelihood of future risky behavior, but flags current activity that falls outside expected norms.
This score isn’t just a number, it’s a prioritization tool for SecOps teams to focus on who needs attention, why, and when. We also enable our customers to flag risky users and add them to a watchlist, making it even easier to lock down these threats and determine who's a liability.
Summary
Insider threats don’t always look like threats – until it’s too late. In SaaS environments where users, data, and access are constantly in motion, relying on traditional tools or surface-level alerts just isn’t enough.
Whether it’s a negligent employee, a compromised contractor, or a malicious insider, DoControl gives you the visibility and control to act early, and combat these insider threats with confidence.
Want to Learn More About Insider Threats?
ITDR Part #1: Why Identity Is the New Perimeter
ITDR Part #2: Identity Based Threats & How You Can Detect Them from Within
ITDR Part #3: From Reactive to Resilient: Responding to Identity Threats in Real Time

.png)

