In 2026, modern organizations rely on SaaS platforms like Google Workspace, Microsoft 365, and Slack to run their operations. The rise of Software as a Service (SaaS) has reshaped how companies function - bringing scalability, flexibility, and accessibility like never before.
But as cloud adoption accelerates, SaaS security has become a business-critical priority. Organizations must protect sensitive data, manage user access, and prevent configuration errors that could expose valuable assets.
That’s where SaaS Security Posture Management (SSPM) comes into play - helping businesses maintain visibility and control over their ever-expanding SaaS environments.
According to Gartner, businesses worldwide will spend nearly $300 billion dollars on SaaS products by the end of 2025.
According to DoControl data, the average company with over 1000 employees had a staggering 22.8 million SaaS assets.
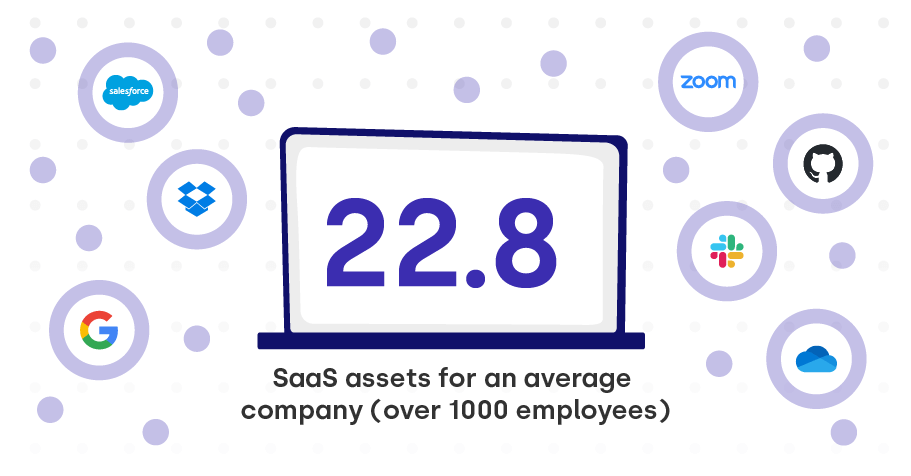
Clearly, this is a significant amount of resources and data to protect, and this is only set to grow in the coming years.
The Significance of SaaS Security
SaaS security is a comprehensive approach to safeguarding data, applications, and user interactions across cloud-based services. It ensures confidentiality, integrity, and availability - three key pillars of cybersecurity.
Unlike traditional perimeter-based security, SaaS security protects assets that live outside corporate networks. It integrates SaaS cybersecurity, data protection, and access governance into one continuous defense layer.
Key benefits include:
- Maintaining business continuity in cloud-first environments
- Upholding customer trust and regulatory compliance
- Preventing insider threats and unauthorized access
When done right, SaaS application security strengthens your organization’s resilience and ensures compliance with key frameworks.
Common SaaS Security Risks and Threats
Every SaaS ecosystem comes with unique risks. Understanding and mitigating them is crucial to building a robust SaaS security posture.
1. Data Breaches
Unauthorized access to SaaS data can cause severe financial and reputational harm. Compromised account takeovers and data breaches often result from lack of identity management, misconfigurations, overexposed sharing, or weak data access controls.
2. Unauthorized Access
Lack of visibility into user behavior can enable insider threats. DoControl data found that 90% of companies had former employees access business assets within Saas applications after they were no longer working at the organization.
Some of those employees even accessed that data two years after leaving the company.
3. Data Loss
Without proper data loss prevention (DLP), organizations risk permanent loss of sensitive data due to user error or malicious activity. An effective SaaS DLP strategy is crucial for any organization operating in the cloud and using SaaS applications as a part of their tech stack.
Data sprawl from these applications can have detrimental effects to an organization’s overall security posture, and business longevity.
4. Third-Party App Vulnerabilities
Unvetted third-party OAuth integrations often introduce hidden risks. DoControl data found that companies using Google Workspace alone installed 2,207 new third-party OAuth apps and issued 42,000 OAuth tokens.
The solution here? Deploying a dedicated SSPM solution to continuously monitor SaaS configurations, third-party app permissions, and risk posture.
Key Areas That Require SaaS Security Protection
To strengthen your SaaS cybersecurity, prioritize visibility and control across four key domains:
1. Configurations and Misconfigurations
Default app settings are often too lax. Proper configuration management ensures least privilege access, compliant sharing policies, and real-time alerts for misconfigurations.
2. Data Protection and Privacy
Your SaaS apps store sensitive data - financial records, customer details, and internal communications. Implement encryption, data discovery tools, and SaaS compliance frameworks to prevent overexposure.
3. User Behavior and Access Controls
Employees can be your weakest link or strongest defense. Enable multi-factor authentication (MFA), monitor user activity, and deploy behavior analytics to detect risky actions.
4. Third-Party App Security
Third-party apps increase convenience - but also risk. Vet all integrations, review permissions regularly, and revoke unnecessary access. Continuous monitoring ensures compliance and reduces shadow IT exposure.
SaaS Security Checklist for Organizations
A proactive SaaS security framework helps you measure and improve your posture. Use this checklist to guide your efforts:
- Data Encryption: Secure data in transit and at rest. Regularly rotate encryption keys.
- Access Controls: Enforce role-based granular access controls and continuously review permissions.
- Authentication Methods: Enable MFA and promote strong password hygiene.
- Data Backup and Recovery: Automate backups and test recovery workflows.
- Security Monitoring: Implement real-time alerts and anomaly detection.
- Vulnerability Management: Scan for SaaS misconfigurations and patch promptly.
- User Education: Train employees on SaaS cybersecurity best practices and phishing prevention.
- Incident Response: Maintain a tested, documented incident response plan.
- Third-Party Risk Management: Audit external vendors for compliance and security certifications.
- Compliance: Align with GDPR, SOC 2, and ISO 27001 standards.
Benefits of a Strong SaaS Security Posture
A mature SaaS cybersecurity strategy yields measurable business benefits:
- Enhanced Compliance: Stay aligned with evolving privacy laws.
- Customer Trust: Strong SaaS security demonstrates responsibility and transparency.
- Business Continuity: Minimize downtime, data loss, and recovery costs.
- Operational Efficiency: Automation and continuous monitoring reduce manual overhead.
Ultimately, investing in SaaS security posture management not only prevents breaches - it supports long-term business resilience.
Emerging Trends in SaaS Security (2026 and Beyond)
The SaaS threat landscape is evolving each day - especially as new AI tools and applications are entering the fold. Key trends shaping the next era include:
- AI-driven threat detection for faster anomaly response.
- Zero Trust architecture adoption across SaaS ecosystems.
- AI browser extensions and third-party tools as a top SaaS attack vector.
- Generative AI (tools like Gemini, Copilot, Glean) data exposure mitigation.
- Continuous compliance automation through SSPM tools.
Organizations that stay ahead of these trends will maintain both security and agility in the cloud era.
Final Takeaways
In an era where data has become one of the most valuable business assets, SaaS security stands as the first line of defense against ever-evolving cyber threats.
To stay protected, organizations must continuously assess risks, adopt a comprehensive SaaS security framework, and take proactive steps toward data loss prevention (DLP), access governance, shadow app management, identity threat detection and response (ITDR), and regulatory compliance.
While SaaS solutions deliver unmatched scalability, flexibility, and efficiency, they also introduce new and complex cybersecurity challenges. Success in the cloud era requires more than reactive defenses - it demands an adaptive, forward-looking security strategy.
The convergence of SaaS innovation and cybersecurity resilience defines the modern digital enterprise. This intersection is where protection meets progress - and where organizations that prioritize SaaS security can confidently innovate, operate, and grow in a connected world.
FAQs About SaaS Security
Q1: What is SaaS security and why is it important?
SaaS security protects data, users, and applications within cloud-hosted software. It prevents breaches, ensures compliance, and maintains business continuity.
Q2: What are the most common SaaS security risks?
The biggest threats include data breaches, misconfigurations, insider access, and insecure third-party integrations.
Q3: What is SaaS Security Posture Management (SSPM)?
SSPM continuously monitors your SaaS apps for misconfigurations, compliance gaps, and access risks - helping maintain a strong security posture.
Q4: How do I improve SaaS data security?
Enable MFA, encrypt sensitive data, monitor user behavior, and regularly audit app permissions.
Q5: How does SaaS security differ from traditional cybersecurity?
Unlike traditional on-premise security, SaaS security focuses on protecting applications hosted in the cloud - requiring visibility, automation, and configuration management.


.png)
