Manifesto


The world has fundamentally changed in how we operate day-to-day business processes.
Traditionally, sharing data meant downloading a file and then uploading it to an email or a secure file-sharing system. While that still occurs, it’s no longer the most common approach. Today, data is shared primarily through cloud-based collaboration platforms such as Google Workspace and Microsoft 365.
This shift has enabled extraordinary acceleration in both internal and external business collaboration. The ability for multiple users to access and edit a single document in real time is transformative. However, this evolution has also created a gap in understanding how data is being shared and how to properly protect it. Organizations increasingly recognize that external sharing, in particular, introduces significant risk. Consider financial data becoming publicly exposed or proprietary code shared inappropriately.
Yet legacy systems and native platform controls rely on a rigid, binary approach: scan the data, identify sensitive content, and block or allow the share. To make matters worse, these controls often rely on agent-based or pull-based mechanisms, making them slow and prone to missing critical incidents. This simplistic and inflexible model does not align with the nuanced detection businesses need. More importantly, it frequently blocks legitimate business activity - slowing productivity, frustrating users, hindering operations, and ultimately impacting revenue.
This challenge is especially visible in organizations leveraging Google Workspace, where cloud-native collaboration is part of the culture and where Google offers limited capabilities to manage or govern this sharing behavior.
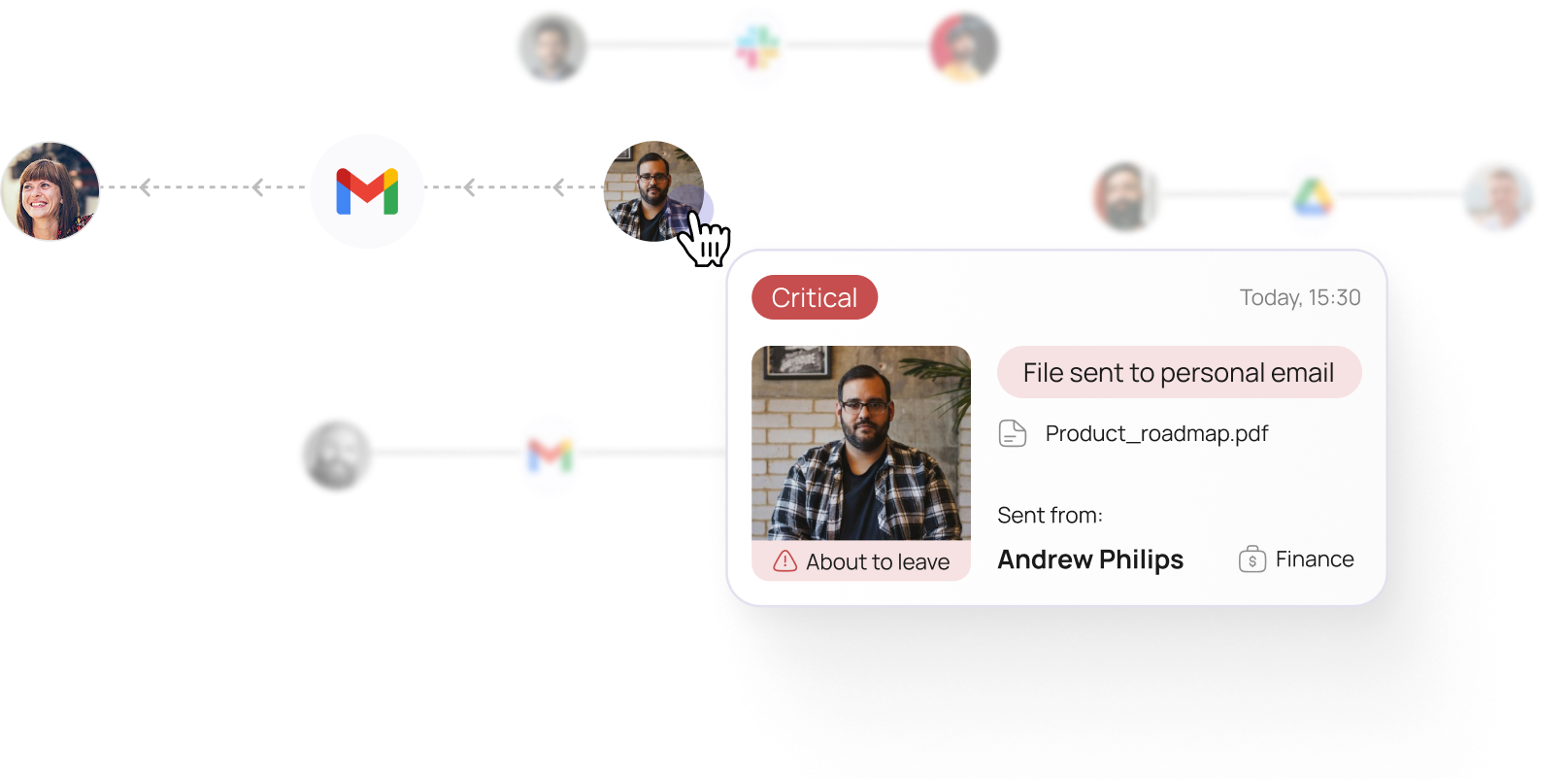
What’s missing is the ability to combine content analysis with the most critical dimension of all: user and identity context. Who is the data being shared with? Who is the user initiating the share? Are they an employee on a performance plan, a departing employee, a former contractor, or an unauthorized third party? Identity context provides a full picture around each sharing event - enabling a true distinction between risky and non-risky activity.
For example, imagine a CFO sharing the company’s financial plan with Deloitte. Deloitte is a trusted domain because they are the audit firm. Traditional DLP would block this action due to the highly sensitive data, without recognizing that the CFO is authorized and that the recipient is a trusted third party - disrupting legitimate business.
Conversely, consider an employee who is about to leave the company sharing a file named “Product Roadmap” to their personal email so they can take it to their new employer. Traditional DLP would likely miss this because the file contains no PHI or PII to trigger a rule, and it cannot identify that this user is about to depart - allowing critical proprietary information to walk out the door.
DoControl was built to solve this challenge. We developed a deep engine that unifies sharing activity, user and identity intelligence, and content analysis - triggering data scans only when context requires it. This contextualized exposure analysis enables precise alerting and dynamic, granular automated policies that align with real business processes - allowing organizations to engage end users directly - ensuring security controls do not hinder productivity.
Companies should never have to compromise productivity for security. They should feel confident that risks are not slipping through the cracks because a critical part of the puzzle - identity and user context - is missing.
DoControl believes data sharing is the foundation of SaaS security. Protecting an organization’s most critical data must come first, and additional modules - such as Shadow Apps and Misconfiguration analysis - serve as powerful, complementary capabilities. Together, they provide a comprehensive solution that enables organizations to address all of their SaaS security needs.
Get updates to your inbox



.png)
